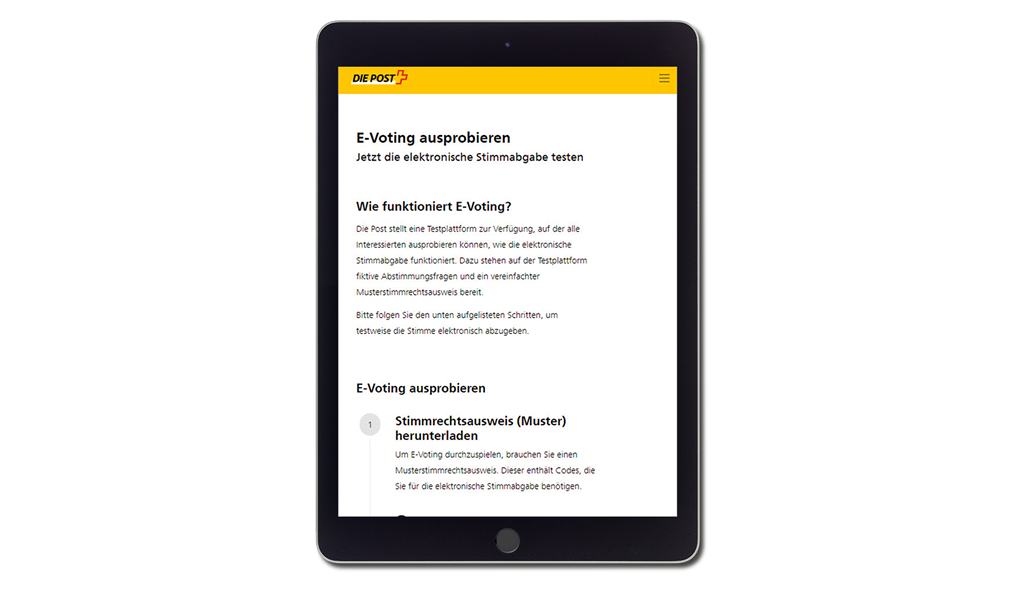
Whenever Runer Jonsson’s stories about “Vicky the Viking” mention that Sven the Terrible’s ship is on the horizon, there seems to be no way out for the inhabitants of the Viking village of Flake. Sven the Terrible is too big and strong, his intentions too evil and sneaky, the spikes of his flail too pointed and sharp and the warriors on his ship too numerous and determined. The fate of Flake seems sealed.
In every hopeless situation, however, the clever Viking boy Vicky succeeds in saving his village from Sven the Terrible with a brilliant idea. The leader of Flake, Vicky's father Halvar, is very sceptical, but he has no choice but to help implement Vicky’s plan. Halvar only gradually notices that this is actually working, when Sven’s attacks are ineffective and he finally has to return home. Because Vicky's ideas are original and surprising, the attackers encounter a defence strategy that their weapons cannot counteract.
The same is true of e-voting in Switzerland, when powerful countries such as Russia, China or the USA have an interest in a particular outcome of a federal vote. These countries are too big and too strong, their intentions too evil and malicious, their technologies too powerful and too advanced and the hackers who are hired by these countries too numerous and too sophisticated. The fate of democracy in Switzerland seems sealed.
Despite this huge danger, the Federal Council continues its strategy of gradually introducing electronic voting. It draws upon on the many brilliant ideas that have been developed in 30 years of e-voting research. This branch of applied cryptography is based on an assumption that it is dealing with the strongest possible attacker.
The latter tries to attack the electoral system on all possible levels. So basically everything is insecure: the hardware, the software, the network, the central infrastructure, and even the people who run the system. In spite of these adverse conditions, is it still possible to completely prevent undetected election manipulation?
It’s a very interesting scientific question, which requires closer examination. Without stopping to consider the issue in depth, critics tend to react prematurely and answer the question with “no”. Just like Halvar, Snorre and Faxe, who are initially very sceptical about Vicky's ideas because they cannot understand his lateral thinking. But at least they do not reject Vicky’s ideas from the beginning.
Probably the most important idea that has emerged from e-voting research is that of universal verification (also called universal verifiability). Its aim is to provide the electorate with a means of independently verifying the election result. The methods used are designed in such a way that all conceivable manipulation attempts are revealed during verification at the latest. The cryptographic methods used guarantee this with mathematical precision.
There is something similar in traditional elections and votes on paper. If there are doubts about the result of the election, for example if the result is very close, a recount can be requested. Since there are always minor discrepancies in the manual counting of ballots, the result of the recount will never be exactly the same, but in most cases it will suffice to confirm the winners of the election.
Universal verification of electronic voting goes one step further. The cryptographically protected data which is aggregated in the preparation, execution and counting of a vote in a distributed system serves as input for universal verification. In this case, a recount is performed, so to speak, whereby every little discrepancy in the data is revealed during the verification. This mechanism makes it impossible for manipulations to go undetected. In turn, successful universal verification eliminates any doubt about the correctness of the count. There are no minor discrepancies such as with counting paper ballots.
The discussion about the security of e-voting has recently been shaped by those who reject the introduction of e-voting in Switzerland on the basis of fundamental convictions. In most cases, their reasoning is relatively thin, because it essentially consists of exactly the attack scenarios that have driven e-voting research for 30 years. However, the critics do not seem to be really familiar with the results of this research.